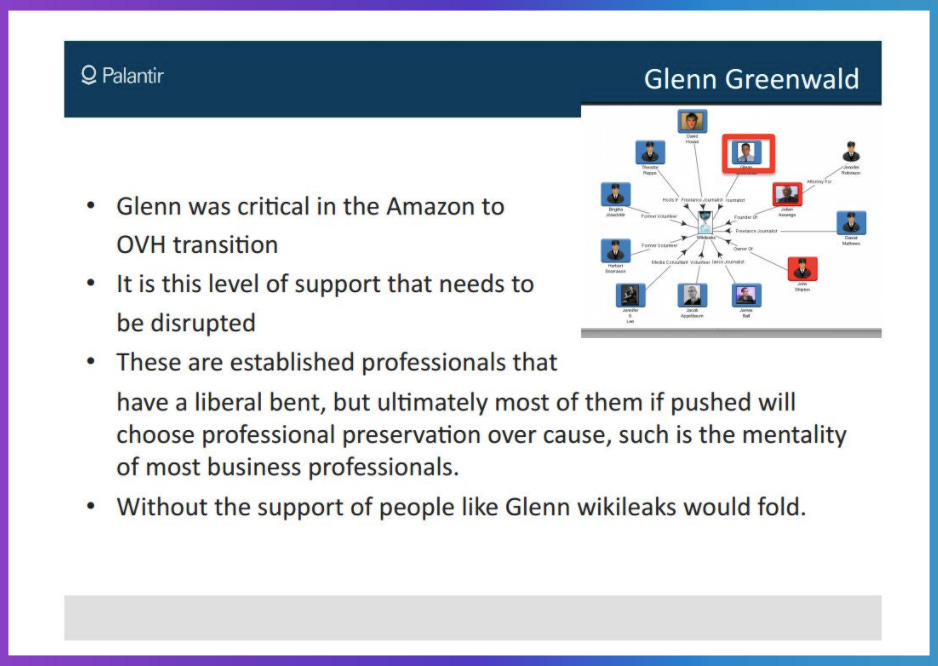
talkliberation | In a document titled The WikiLeaks Threat: An Overview authored by Palantir Technologies in conjunction with HBGary Federal and Berico Technologies, a slide centrally featuring the WikiLeaks logo depicts spokes leading to key public supporters. Notes at the bottom of the slide outline the corporate grievances in play, decrying “established professionals… with a liberal bent” and declaring that “this level of support needs to be disrupted”. The final line reads “without the support of people like Glenn, WikiLeaks would fold”.
What folded, in fact, was very nearly HBGary itself. CEO and minority shareholder Aaron Barr stepped down in disgrace.
It wouldn’t be the first time or the last that Greenwald would be targeted in some form for his journalism. That he is also named (and even central) in some of the new #WLDragnet documents, will likely come as no surprise.
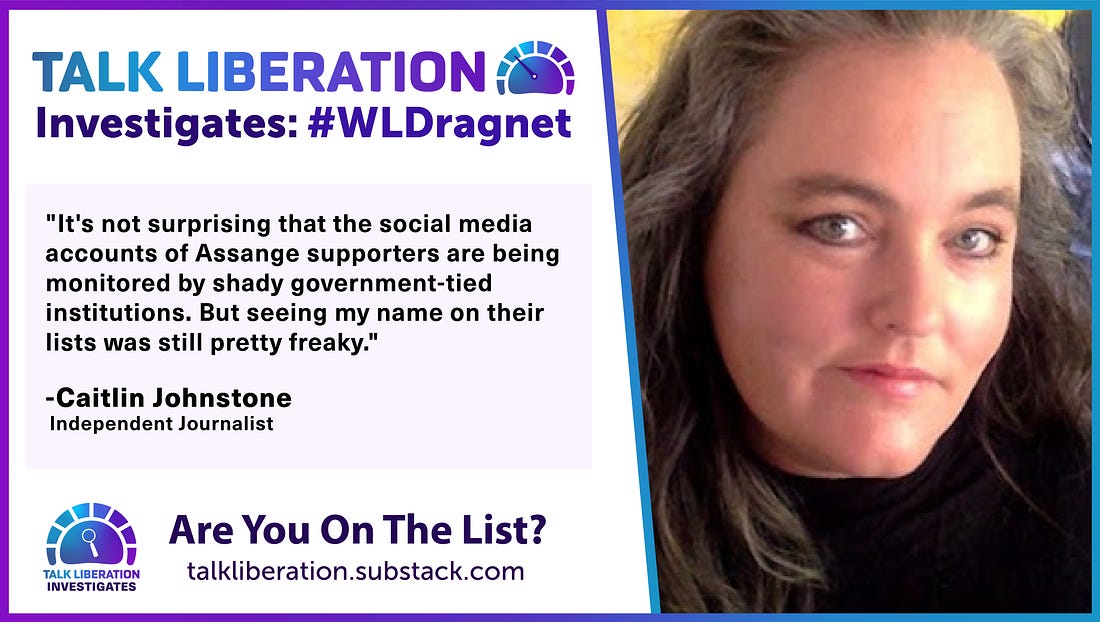
Nor to the other influencers identified in the documents. Popular Australian independent journalist Caitlin Johnstone, repeatedly named in the NodeXL files said that it was “not surprising” but “still pretty freaky”.
A who’s who of high profile independent media, whistleblowers and support organizations who stand with Julian Assange and WikiLeaks are named again and again in the #WLDragnet documents.
As are thousands of their followers, members of their personal networks and frankly, damn near anyone with even the vaguest sense of political awareness or understanding as to the historic importance of the battle to save Julian Assange.
It has long been assumed by all and sundry that only WikiLeaks staff, closest collaborators or other persons of significance could be plausibly caught in such a web. That those possessing insider knowledge, occupying positions of some influence or power, or with the ability to extend significant social reach were the logical focal targets of state-led efforts to clip the wings of WikiLeaks.
But new evidence points to a truly global network of digital repression targeted at WikiLeaks supporters who possess little if any such secret knowledge, significance or power. The documents we are publishing, sourced from publicly available data, contain the social media user account handles of hundreds of members of the public, with thousands collected on.