Tuesday, March 27, 2018
With "Platform" Capitalism - Value Creation Depends on Privacy Invasion
By
CNu
at
March 27, 2018
0
comments
![]()
Labels: facebook IS evil , governance , Livestock Management , neofeudalism , shameless , TIA , Toxic Culture? , transbiological , tricknology
Saturday, March 24, 2018
Atlanta Had Bad Backups and No Kaspersky...,
By
CNu
at
March 24, 2018
0
comments
![]()
Labels: count zero , FAIL , tricknology
Friday, March 23, 2018
Facebook the Surveillance and Social Control Grail NOT Under Deep State Control
By
CNu
at
March 23, 2018
0
comments
![]()
Labels: AI , clampdown , Deep State , disinformation , dopamine , hegemony , information , Livestock Management , politics , quorum sensing? , TIA , tricknology
Tuesday, March 06, 2018
On Second Thought, Propagation of the Faith May Be Even More Fundamental...,
By
CNu
at
March 06, 2018
0
comments
![]()
Labels: alkahest , azoth , cognitive infiltration , Pimphand Strong , propaganda , reality casualties , sum'n not right , tricknology , unspeakable
Protecting Profit Is The Fundamental Objective
By
CNu
at
March 06, 2018
0
comments
![]()
Labels: corporatism , information anarchy , professional and managerial frauds , profitability , tricknology , truth
Saturday, March 03, 2018
Why Would The U.S. Govt Fund TOR/Dark Web If These Limited Its Power?
By
CNu
at
March 03, 2018
0
comments
![]()
Labels: cognitive infiltration , information anarchy , TIA , tricknology
Snitches Don't Get Stitches, They Get Gubmint Jobs....,
The pitch, a joint venture with a now-defunct company called HBGary Federal and the Peter Thiel-backed company Palantir Technologies, however, crumbled in 2011 after it was exposed in a series of news reports.
The biography section of Ryan’s campaign website references only another technology business he helped found, called Second Front Systems. That company deploys “cutting-edge data analytics software to our troops on the front lines,” according to the site. Ryan continues to own a 10 percent stake in the firm, valued between $15,000 and $50,000, and has discussed his work with the startup as part of his experience of building a business and providing jobs.
By
CNu
at
March 03, 2018
0
comments
![]()
Labels: Ass Clownery , professional and managerial frauds , TIA , tricknology
Thursday, January 18, 2018
Bitshit: BUY! BUY! BYE!
The reason for halt of lending and exchange platform has many reasons as follow:
The continuous bad press has made community members uneasy and created a lack of confidence in the platform.
We have received two Cease and Desist letters, one from the Texas State Securities Board, and one from the North Carolina Secretary of State Securities Division. These actions have become a hindrance for the legal continuation of the platform.
Outside forces have performed DDos attacks on platform several times and have made it clear that these will continue. These interruptions in service have made the platform unstable and have created more panic inside the community.
Many in the cryptocurrency community have openly accused Bitconnnect of running a Ponzi scheme, including Ethereum founder Vitalik Buterin.
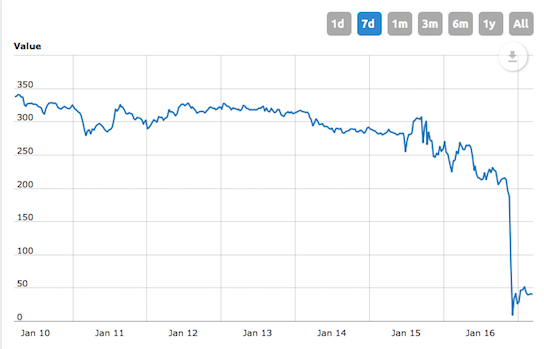
The platform was powered by a token called BCC (not to be confused with BCH, or Bitcoin Cash), which is essentially useless now that the trading platform has shut down. In the last The token has plummeted more than 80% to about $37, down from over $200 just a few hours ago.
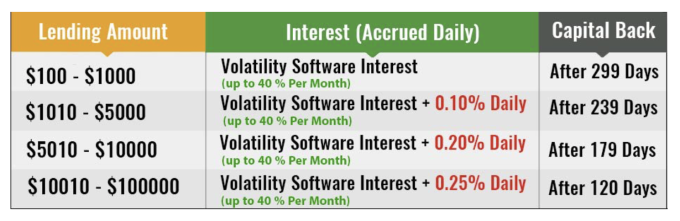
If you aren’t familiar with the platform, Bitconnect was an anonymously-run site where users could loan their cryptocurrency to the company in exchange for outsized returns depending on how long the loan was for. For example, a $10,000 loan for 180 days would purportedly give you ~40% returns each month, with a .20% daily bonus.
Bitconnect also had a thriving multi-level referral feature, which also made it somewhat akin to a pyramid scheme with thousands of social media users trying to drive signups using their referral code.
The platform said it generated returns for users using Bitconnnect’s trading bot and “volatility trading software”, which usually averaged around 1% per day.
Of course profiting from market fluctuations and volatility is a legitimate trading strategy, and one used by many hedge funds and institutional traders. But Bitconnect’s promise (and payment) of outsized and guaranteed returns led many to believe it was a ponzi scheme that was paying out existing loan interest with newly pledged loans.
The requirement of having BCC to participate in the lending program led to a natural spike in demand (and price) of BCC. In less than a year the currency went from being worth less than a dollar (with a market cap in the millions) to a all-time high of ~$430.00 with a market cap above $2.6B.
Bitconnect is officially closing up. They sent me 33 BCC for my $11k+ in loans. Worth $6600 and dropping by the second. Their exchange is down so the only option is to send the BCC to an external exchange.— LifeByAdam (@LifeByAdam1) January 16, 2018
By
CNu
at
January 18, 2018
0
comments
![]()
Labels: Dystopian Now , FAIL , fraud , hustle-hard , parasitic , professional and managerial frauds , reality casualties , tricknology
Wednesday, January 17, 2018
Your Elites Are Like A Parasite About To Kill Its Host
By
CNu
at
January 17, 2018
0
comments
![]()
Labels: alkahest , azoth , banksterism , Breakaway Civilization , parasitic , shameless , tricknology
Wednesday, January 10, 2018
Money As Tool, Money As Drug: The Biological Psychology of a Strong Incentive
By
CNu
at
January 10, 2018
0
comments
![]()
Labels: addiction , banksterism , debt slavery , dopamine , hegemony , human experimentation , hypnosis , transbiological , tricknology , What IT DO Shawty...
Wednesday, January 03, 2018
You Know Better Than To Use Browser Password Managers..., Right?
By
CNu
at
January 03, 2018
0
comments
![]()
Labels: tricknology , wikileaks wednesday
Monday, December 18, 2017
The Long Leash
By
CNu
at
December 18, 2017
0
comments
![]()
Labels: cognitive infiltration , Collapse Crime , cull-tech , high strangeness , human experimentation , information anarchy , Living Memory , necropolitics , nootropism , normotic illness , tricknology , What IT DO Shawty...
Thursday, December 14, 2017
Backpropagation: The Beginning of a Revolution or the End of One?
By
CNu
at
December 14, 2017
0
comments
![]()
Labels: AI , count zero , tricknology , What Now?
Sunday, December 10, 2017
Next Up: Ekmanized Pre-Cog Face-Reading AI...,
By
CNu
at
December 10, 2017
0
comments
![]()
Labels: AI , cognitive infiltration , disintermediation , Livestock Management , subliminal , tricknology
Thursday, December 07, 2017
3-D Printed, WiFi Connected, No Electronics...,
By
CNu
at
December 07, 2017
0
comments
![]()
Labels: Exponential Upside , Noo/Nano/Geno/Thermo , transbiological , tricknology , unintended consequences , What Now?
3-D Printed Living Tattoos
By
CNu
at
December 07, 2017
0
comments
![]()
Labels: Exponential Upside , Noo/Nano/Geno/Thermo , transbiological , tricknology , What Now?
Sunday, November 19, 2017
Weaponization of Monetization? Nah, Just Look In the Mirror For the Problem...,
By
CNu
at
November 19, 2017
0
comments
![]()
Labels: American Original , FRANK , subliminal , tactical evolution , tricknology
Tuesday, November 14, 2017
CIA False-Flagging and Impersonating Kaspersky
By
CNu
at
November 14, 2017
0
comments
![]()
Labels: count zero , Deep State , disinformation , predatory militarism , tricknology , you used to be the man
Friday, October 27, 2017
CIA-BezosPost Wants To Come Inside Without A Warrant
- The "employee" (really a contractor, by the way) for Amazon simply steals anything he or she wants in your house while making the delivery -- which you allowed them in for.
- Your credit card gets compromised. Said individual orders something on your card to your house, waits for it to be delivered inside and exploits said delivery, either in confederation with the person doing it or by rick-rolling them, and robs your house.
- The access code is stolen and used to directly access your home. It's in the cloud. I'm sure nothing in the cloud will ever be stolen, right? Uh huh, just like virtually every American's credit file wasn't? And since the code used to open the door will be authorized guess what -- your high-fautin' security system won't raise a peep as your nice 60" 4k OLED TV and jewelry walk right out the front door!
By
CNu
at
October 27, 2017
0
comments
![]()
Labels: Ass Clownery , conspicuous consumption , corporatism , doesn't end well , sum'n not right , tricknology
Wednesday, October 11, 2017
Trans-Turing Trains Silly Monkey Brains
By
CNu
at
October 11, 2017
0
comments
![]()
Labels: as above-so below , cognitive error , cognitive infiltration , ethology , killer-ape , propaganda , status-seeking , tricknology , unintended consequences , wikileaks wednesday
Self-Proclaimed Zionist Biden Joins The Great Pretending...,
Biden, at today's Holocaust Remembrance Ceremony, denounces the "anti-Semitic" student protests in his strongest terms yet. He...
-
theatlantic | The Ku Klux Klan, Ronald Reagan, and, for most of its history, the NRA all worked to control guns. The Founding Fathers...
-
Video - John Marco Allegro in an interview with Van Kooten & De Bie. TSMATC | Describing the growth of the mushroom ( boletos), P...
-
Farmer Scrub | We've just completed one full year of weighing and recording everything we harvest from the yard. I've uploaded a s...